Security and Compliance
Security and Compliance
Petronella Technology Group, Inc. serves customers who are affected by security and compliance regulations across many vertical sectors in both public and private organizations. We understand that every industry and organization can be faced with unique IT challenges. We understand security and compliance.
Our expertise enables us to help clients navigate the requirements of their industry – such as HIPAA, HITECH, Sarbanes, Oxley, DFARS, and NIST – to find a solution that meets their needs. We will partner with you to design, implement, and support a solution that meets your specific requirements.
We should be fair, and say that at the time of this update, the organizations that enforce these compliance requirements don't know how to secure even themselves. But they will unleash their justice upon you, and it may feel more like their fury.
For HIPAA, the U.S. Department of Health and Human Services (HHS) couldn't prevent a data breach of their own records if the right hacker group was motivated enough.
Neither could the Office for Civil Rights (OCR), the auditing arm of the HHS. But they will sure punish you if you are the victim of a data breach. They won't only punish you, they will shame you as well- on their "Wall of Shame" (true story). See the breach portal at https://ocrportal.hhs.gov/ocr/breach/breach_report.jsf.
But that's just HIPAA. Based on NIST 800-53 and NIST 800-171, the NSA should be fined for getting hacked and unleashing their beastly hacking tools upon the world. We haven't heard of any penalty imposed upon the NSA, as of yet.
But don't expect the same free pass. In the world of 3-letter groups, us commoners are not VIP.
But in the words of Marcus Tullius Cicero, "Live as brave men; and if fortune is adverse, front its blows with brave hearts."
Which might be the best you can do, if you are subject to security and compliance regulations but are not prepared for an audit. Audits are already underway from several different federal rule enforcement agencies.
Click here to signup for your Basic Security Checkup.
Security and Compliance Areas
Government contractors may face compliance concerns when working with Federal Government customers. Regulations such as NIST 800-171, Defense Federal Acquisition Regulation Supplement (DFARS), and NIST 800-53, which is part of the Federal Information Security Management Act (FISMA), are often a component of the technology standards that government contractors must follow during their work.
To ensure full compliance with DFARS and FISMA requirements, contractors should understand what each regulation covers, the systems that they apply to, and whether overlap occurs between them.
We are proficient with security and regulatory compliance issues such as:
Defense Federal Acquisition Regulation Supplement (DFARS) & NIST 800-171
NATIONAL INSTITUTE OF STANDARDS AND TECHNOLOGY (NIST) SPECIAL PUBLICATION (SP) 800-171, "PROTECTING CONTROLLED UNCLASSIFIED INFORMATION IN NONFEDERAL INFORMATION SYSTEMS AND ORGANIZATIONS", https://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-171.pdf
https://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-171.pdf
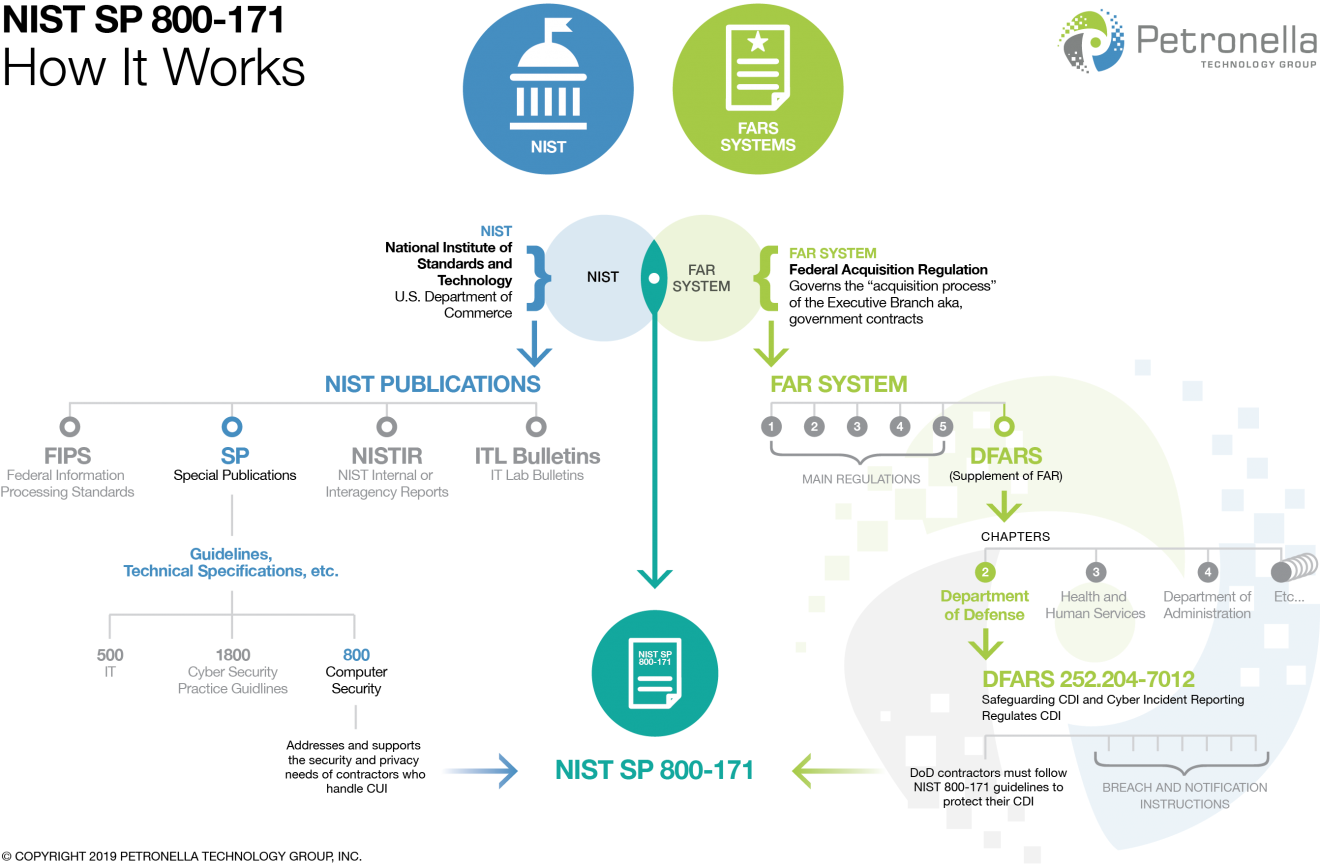
Federal Information Security Management Act (FISMA) NIST 800-53 Security Controls
HIPAA & HITECH: The Health Insurance Portability and Accountability Act of 1996 (HIPAA; Pub.L. 104-191, 110 Stat. 1936, enacted August 21, 1996) was enacted by the United States Congress and signed by President Bill Clinton in 1996.
GLBA: The Gramm-Leach-Bliley Act (GLBA), also known as the Financial Services Modernization Act of 1999, (Pub.L. 106-102, 113 Stat. 1338, enacted November 12, 1999) is an act of the 106th United States Congress (1999-2001).
California Consumer Privacy Act of 2018 (CCPA): On June 28, 2018 California legislature passed AB 375, the California Consumer Privacy Act of 2018, effective January 1, 2020.
If the law is not amended before it becomes effective, The California Consumer Privacy Act, AB. 375 — gives California residents an array of new rights, starting with the right to be informed about what kinds of personal data companies have collected and why it was collected.
GDPR: General Data Protection Regulation: The General Data Protection Regulation (GDPR) (EU) 2016/679 is a regulation in EU law on data protection and privacy for all individuals within the European Union and the European Economic Area. It also addresses the export of personal data outside the EU and EEA.
The GDPR aims primarily to give control to citizens and residents over their personal data and to simplify the regulatory environment for international business by unifying the regulation within the EU.
ISO 27001, ISO 27002, SOC 1, SOC 2, SOC 2 Type II, SOC 3, HIPAA, HITRUST, GLBA, PCI, FACTA, SOX, FERPA, Sarbanes-Oxley, SOX, FDA 21 CFR PART 11 (Electronic Records) & 21 CFR 820 (Quality Systems), NIST SP 800, ISO 27001-2013, FedRAMP, COBIT, SSAE16.
PCI: The Payment Card Industry Data Security Standard (PCI DSS) is a set of security standards designed to ensure that ALL companies that accept, process, store or transmit credit card information maintain a secure environment.
FACTA: FACTA (Fair and Accurate Credit Transactions Act) is an amendment to FCRA (Fair Credit Reporting Act ) that was added, primarily, to protect consumers from identity theft.
SOX: The Sarbanes-Oxley Act of 2002: (Pub.L. 107-204, 116 Stat. 745, enacted July 30, 2002), also known as the "Public Company Accounting Reform and Investor Protection Act" (in the Senate) and "Corporate and Auditing Accountability and Responsibility Act" (in the House) and more commonly called Sarbanes-Oxley, Sarbox or SOX.
FERPA: The Family Educational Rights and Privacy Act (FERPA) (20 U.S.C. § 1232g; 34 CFR Part 99) is a Federal law that protects the privacy of student education records. The law applies to all schools that receive funds under an applicable program of the U.S. Department of Education.
We can support these with our commitment to process and procedure improvements (ISO 20000, ISO 27001, ISO 27002, etc.).
Our CISSP Certified Security and Compliance team is under the direction of an ISACA-Certified Information Systems Auditor who coordinates and provides security and compliance assessments and consultations.
Advantages
- Knowing a facility’s compliance for administrative, physical, and technical aspects
- Knowing the security of your network, data, and devices
- Avoiding the steep fines associated with non-compliance
- Establishing and maintaining the image of a well-run, compliant facility
- Lowering your risk level for disastors such as ransomware attack as your overall security improves, and you become more compliant
Personally identifiable information (PII) is any data that could potentially identify a specific individual. Any information that can be used to distinguish one person from another and can be used for de-anonymizing anonymous data can be considered PII.
If a business or practice uses tablets and smartphones for personal identifiable information, our optional patented software and Mobile Device Management Assessment can protect, identify, and recommend best practices. The threat of ransomware catapults security and compliance to the top of the urgent list for every business.
Regulated industry compliance with security standards is essential, more than ever before.
Click here to signup for your Basic Security Chere
For more of our insights into the topic of Compliance:
https://petronellatech.com/hipaa/
https://petronellatech.com/blog/hipaa/hipaa-breach-notification-rule/
https://petronellatech.com/blog/hipaa/hipaa-compliance/
https://petronellatech.com/blog/hipaa/hipaa-privacy-rule/
https://petronellatech.com/blog/hipaa/hipaa-training/
https://petronellatech.com/blog/hipaa/hipaa-violations-fines/
https://petronellatech.com/blog/hipaa/hitech-act/
https://petronellatech.com/blog/hipaa/ransomware/
Ask us questions on our courtesy HIPAA forum:
Ask us questions on our courtest NIST forum:
You can order discreetly and directly at:
https://itsupport.infusionsoft.app/app/storeFront/showStoreFront
Email us:






