Penetration Testing
You haven't been hacked... Yet!!
Is this keeping you up at night?
IT SHOULD BE.
Here Are the Facts Every Business Faces
Penetration Testing: An Essential Guide to Enhancing Cybersecurity
---
**Meta Description:** Dive deep into the world of penetration testing to understand its importance, types, methodologies, and benefits. Enhance your organization's cybersecurity posture with expert insights.
**Keywords:** Penetration Testing, Cybersecurity, Pen Test Types, Cyber Threats, Ethical Hacking, Vulnerability Assessment
---
### **What is Penetration Testing?**
Penetration testing, often referred to as a 'pen test' or 'ethical hacking', is a cybersecurity practice where experts deliberately target an organization's systems using the same techniques as cybercriminals. The objective? To identify vulnerabilities before malicious actors do.
---
### **Why is Penetration Testing Crucial?**
With cyber threats becoming more sophisticated and frequent, having a robust defense mechanism is paramount. Penetration testing offers a proactive approach, allowing businesses to:
1. **Identify Weaknesses:** Discover vulnerabilities in applications, systems, and networks.
2. **Understand Potential Impact:** Gauge the potential consequences of successful cyber-attacks.
3. **Prioritize Remediation:** Focus resources on addressing the most critical threats.
4. **Maintain Compliance:** Many regulations mandate regular penetration tests.
---
### **Different Types of Penetration Tests**
Penetration testing is not a one-size-fits-all solution. Based on the scope and objectives, pen tests can be categorized as:
1. **Network Testing:** Focuses on finding vulnerabilities in an organization's network infrastructure.
2. **Application Testing:** Targets specific apps, uncovering weaknesses in coding and design.
3. **Physical Testing:** Evaluates physical security measures like locks, CCTV cameras, and access cards.
4. **Wireless Testing:** Concentrates on wireless networks, ensuring they're resilient against attacks.
5. **Social Engineering:** Targets the human element, simulating phishing attacks and pretexting to gauge employee awareness.
---
### **The Penetration Testing Process**
Penetration tests typically follow a structured methodology to ensure comprehensive and consistent results:
1. **Planning & Reconnaissance:** Define the scope, objectives, and gather information about the target.
2. **Scanning:** Utilize tools to identify vulnerabilities in the target system.
3. **Gaining Access:** Attempt to exploit identified vulnerabilities.
4. **Maintaining Access:** Mimic cybercriminal activities by trying to create a persistent presence in the system.
5. **Analysis:** Document findings, provide actionable insights, and suggest remediation measures.
---
### **Benefits of Regular Penetration Testing**
1. **Enhanced Security Posture:** Stay ahead of cybercriminals by regularly updating your defenses.
2. **Cost Savings:** Proactively addressing vulnerabilities can prevent costly breaches.
3. **Stakeholder Confidence:** Assure customers, partners, and stakeholders of your commitment to cybersecurity.
4. **Regulatory Compliance:** Avoid penalties by ensuring compliance with data protection standards and regulations.
---
### **Selecting a Penetration Testing Service**
When choosing a penetration testing service, consider the following:
- **Relevant Experience:** Does the provider have experience in your industry?
- **Tailored Approaches:** Avoid generic services; opt for tailored solutions specific to your organization's needs.
- **Communication:** Ensure the service provider can translate technical jargon into actionable business insights.
- **Tools & Techniques:** A reputable provider should use the latest tools and adhere to industry best practices.
---
### **Penetration Testing vs. Vulnerability Assessment**
It's crucial to differentiate between penetration testing and vulnerability assessments. While both focus on identifying vulnerabilities, a vulnerability assessment offers a snapshot of potential weaknesses without actively exploiting them. In contrast, penetration testing delves deeper, actively trying to exploit these vulnerabilities and assess the potential impact of a breach.
---
### **Conclusion: Safeguarding the Digital Future with Penetration Testing**
In today's hyper-connected digital age, threats lurk at every corner. Penetration testing offers a proactive strategy, allowing organizations to simulate cyber-attacks under controlled conditions. This invaluable insight helps businesses prioritize their resources, ensuring they're well-prepared to fend off actual cyber threats.
**Call to Action:** Are you ready to enhance your organization's cybersecurity posture? Contact our team of expert ethical hackers and fortify your defenses against the ever-evolving landscape of cyber threats.
---
**SEO Elements for the Page:**
- **Title Tag:** Penetration Testing: Essential Guide to Cybersecurity Enhancement
- **H1 Tag:** Penetration Testing: An Essential Guide to Enhancing Cybersecurity
- **Alt Texts:** Images on the page should have alt texts like "Penetration Testing Process", "Types of Pen Tests", "Cybersecurity Defense Layers", etc.
- **Internal Links:** Incorporate internal links to related services or blog posts, such as "Benefits of Cybersecurity", "Understanding Cyber Threats", and "Vulnerability Assessment Services".
- **External Links:** Link to reputable sources discussing cybersecurity standards, regulations, and the latest industry reports.
- **URL Structure:** `https://www.yourwebsite.com/services/penetration-testing-guide`
Remember to keep the content updated, especially in the fast-evolving field of cybersecurity, to maintain its relevance and SEO value.
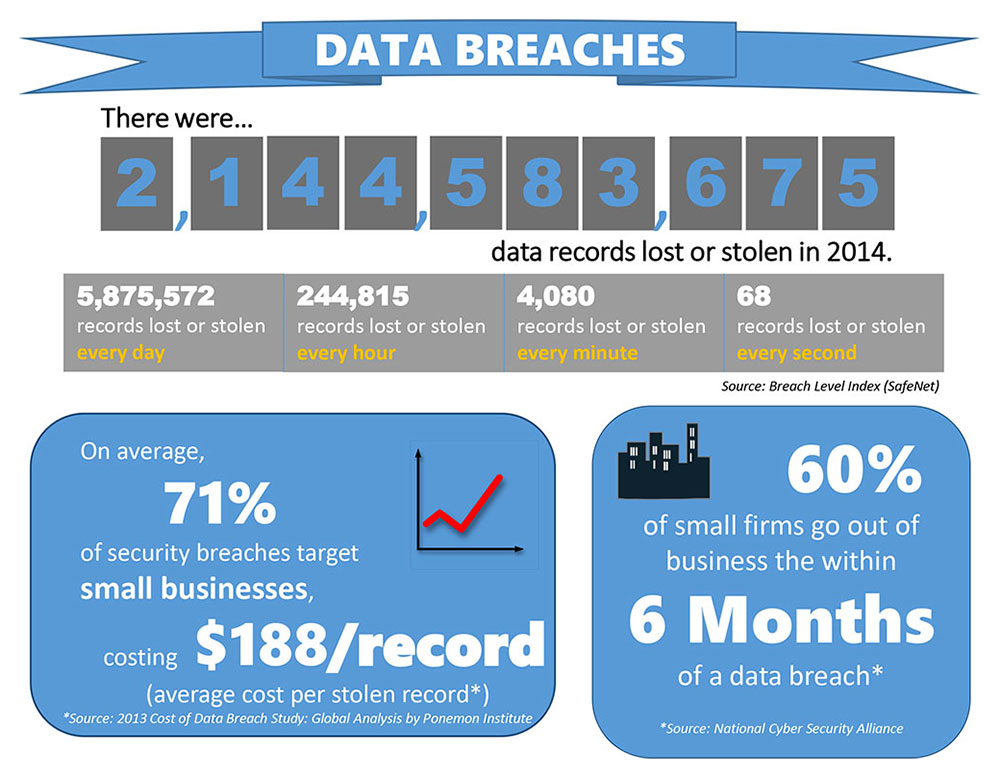
The Value of a Good Assessment and Testing Program Cannot Be Overstated
The benefit of a security assessment a penetration testing program is increased security and security awareness for your organization. It provides you with in-depth, actionable reporting and analysis to facilitate your planning, strategies, and provide practical solutions to your security deficiencies.
You will have a clear understanding of the vulnerabililties of your systems and where you are most likely to experience attacks. You will see with little doubt whether your existing defenses are adequate for protecting your organization against viable attacks.
Your high-risk vulnerabilities will be exposed. The most important benefit is that the knowledge gained will help both management and staff to see the “Security Reality.” It will dispel myths commonly held by organizations with internally mentioned comments like:
- "It couldn't happen to us."
- "We don't have anything worth taking anyway."
- "Our system are adequately protected by our firewalls."

A third party offers an outsider's view. This unbiased, realistic measure of your existing security provided by an expert IT security team can identify potential issues and shed light on vulnerabilities we have seen hackers take advantage of when looking to gain access to business systems.
Then remediation are fairly straight-foward using IT security best practices known to address this shortcomings.
While an IT security assessment and associated penetration testing is the ideal next step for hardening overall security of your organization, a program like that offered by Petronella Technology Group is unmatched in its ability to take action and get a well earned good night's sleep.
Meet Craig Petronella who heads up our IT security team
Craig is an IT Cyber Security Expert who knows how to explain things clearly and implement systems so you and your business are safe. He's a Amazon #1 Best Selling Author as seen on ABC, CBS, NBC, FOX & Newsobserver.com.



Craig Petronella has spent his 23-year computer career supporting such operating systems has Microsoft, Apple, Linux, Unix, and DOS. In addition, he has supported the small business community with the installation and development of complete end-to-end systems.
Craig has made significant inroads in the cybersecurity space and has published pieces in a variety of publications.
Check Out What Others Are Already Saying About Working with
Petronella Technology Group
| I would recommend Petronella Technology Group to any client who is looking for help with IT Security for their practice. I have worked withCraig with the implementation of EMR (Electronic Medical Records) inthe Durham, NC area. He is extremely professional and very knowledgeablewith the current technologies. |
Jaimin Anandjiwala |







